




Discover offensive security resources ranging from reports and guides to our latest webcasts and livestreams.


Securing Airline Commerce: Penetration Testing for AWS Cloud Infrastructure
A major airline technology platform turned to Bishop Fox after routine assessments kept missing the mark. What followed revealed unauthorized PCI database access, misconfigured IAM roles spanning hundreds of instances, and lateral movement across Active Directory domains — driving immediate remediation and stronger customer trust.

Autonomous AI, Broken Guardrails, and Geopolitics
This episode covers autonomous vulnerability discovery, AI agents that ignore instructions, and why models are becoming strategic national assets.
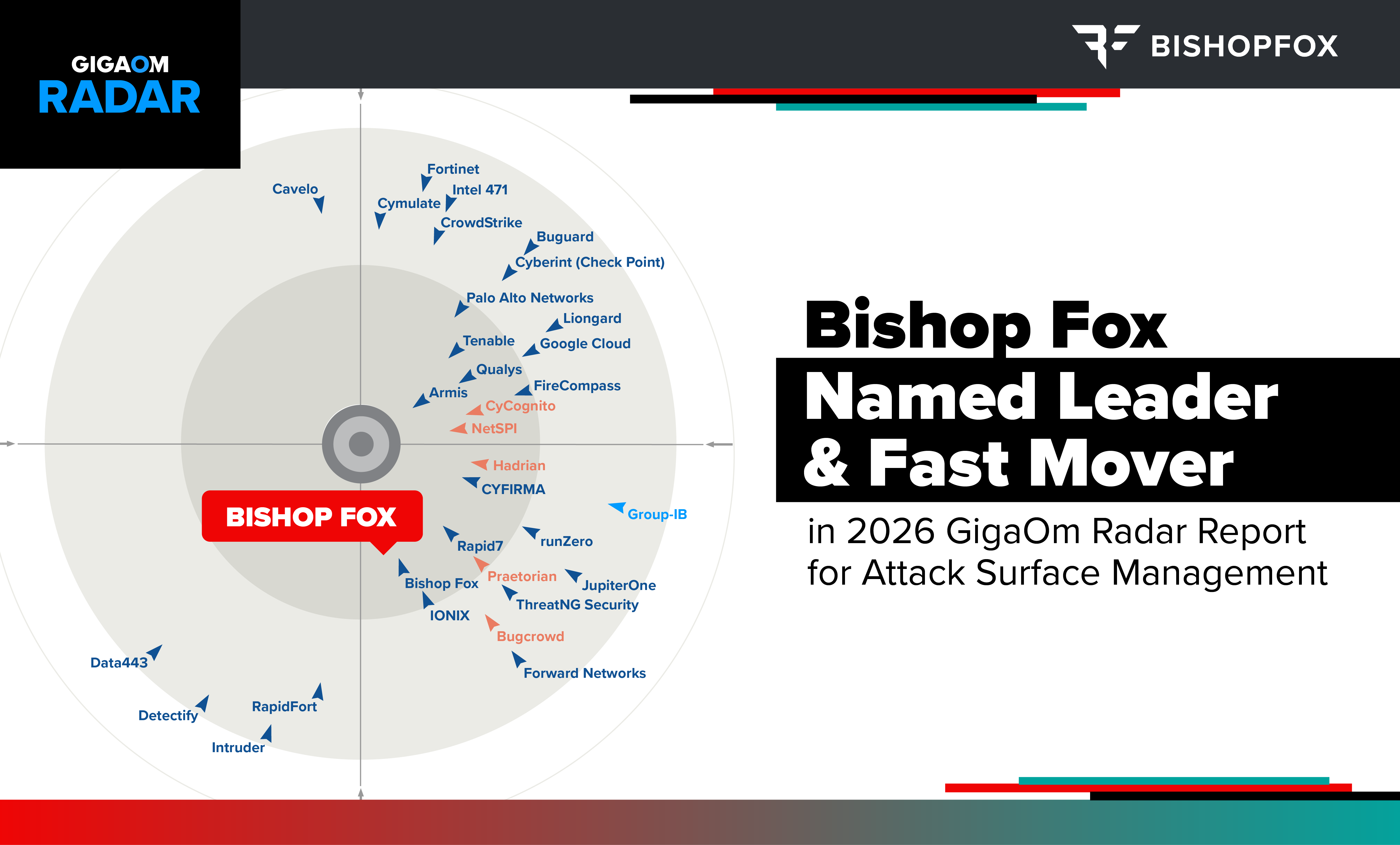
2026 GigaOm Radar for Attack Surface Management
Get an overview of the 2026 Attack Surface Management (ASM) market — along with the key features and business criteria met by the top solutions — and learn why Bishop Fox was named Leader and Fast Mover by the analysts at GigaOm.
The Role of AI in Modernizing Enterprise Application Security
Modern enterprise apps are sprawling, fast moving, and AI accelerated, yet traditional testing cannot keep up. Join this session to learn how AI assisted, expert led testing expands security coverage at scale, improves consistency, and strengthens protection across complex enterprise application portfolios.

SSO Phishing, Patching Failures, Exposed APIs
This episode covers SSO phishing, patching failures, exposed APIs, and zombie infrastructure remind us that basic security hygiene still decides the outcome.

Fueling Security: How a Fortune 500 Utility Stays Ahead of Emerging Threats
A Fortune 500 energy provider faces constant threats from nation-state actors targeting critical infrastructure. Partnering with Bishop Fox for Attack Surface Management and red team assessments, the company gained continuous visibility into their external perimeter...

Deepfakes, Spyware Kits, and LLMs for Hire
This episode covers prompt injection, a hijacked Outlook add-in, commoditized mobile spyware, AI executive deepfake scams, IT-to-OT pivoting, and nation-state use of commercial LLMs to accelerate exploitation.
Building Tools: What, When, and How
Surrounded by security tools but still tempted to “just build it”? This hands-on workshop breaks down when custom tooling is worth it, when it’s not, and how to build fast, focused tools without overengineering.

Red Team Vendor Evaluation Worksheet
The Red Team Vendor Evaluation Matrix Worksheet is designed to help security leaders evaluate red team vendors thoughtfully before engagement using a structured, question-driven approach.
Application Portfolio Penetration Testing Solution Brief
Download our solution brief. Learn how to secure entire application portfolios with attacker-realistic testing and expert-validated, trusted results.

Software Policy Rollbacks, Insider Access Abuse, and AI Automation Risk
This episode covers the rollback of federal software security guidance, insider-driven access risks, ongoing state-sponsored espionage, and the security implications of giving AI tools deep control over infrastructure.

AI & Security Risks: A Cyber Leadership Panel
Watch a fireside chat with cybersecurity and AI leaders on today’s real AI security risks. Learn where risk is emerging, how leaders set ownership, the true cost of securing AI, and practical steps teams use to protect AI systems and data.

Prompt Injection, Session Hijacking, and Why AI Isn't Writing the Attack Plans Yet
This episode covers AI prompt injection risks, continued social engineering via LinkedIn and QR codes, credential theft and session hijacking, patch reliability and appliance security, and how AI is being used to accelerate malware development—distinguishing meaningful risk from overhyped claims.

Application Security: Getting More Out of Your Pen Tests
Application pen tests cost real time and money. Learn how to get real value from them. Bishop Fox lead researcher Dan Petro explains what good app tests include, how to evaluate AI-powered testing, and the questions that matter before and after an engagement.

Fortifying Your Applications: A Guide to Penetration Testing
Download this guide to explore key aspects of application penetration testing, questions to ask along the way, how to evaluate vendors, and our top recommendations to make the most of your pen test based on almost two decades of experience and thousands of engagements.

Sliver Workshop Part 3: Building Better Encoders
In our third Sliver workshop, we explore how Sliver handles traffic encoding by default and how attackers can extend its capabilities with custom Wasm-based encoders. We dive into Sliver’s encoder framework works, what’s possible with WebAssembly, and how to design and test your own encoders.

Red Teaming: The Essential Tool for Security Leaders
Watch Trevin Edgeworth, Red Team Practice Director at Bishop Fox, in this virtual session where he will break down how Red Teaming gives leaders the clarity, evidence, and narrative they need to make informed, high-stakes decisions in the current AI landscape.

Peeling Back the Plastic: Finding 0-Days in IoT Devices
Join Senior Security Consultant Nick Cerne for “Peeling Back the Plastic: Finding 0-Days in IoT Devices” on Tuesday, Nov. 18. Learn hands-on techniques for uncovering hidden vulnerabilities in consumer IoT devices and advancing your IoT security research skills.

Product Security Reviews: The Basics Are Still the Breach
The Product Security Reviews Report is a data-driven analysis that distills two years of hands-on testing across healthcare, IoT, industrial, and financial systems into a single, sobering insight: attackers don’t need sophistication when simplicity still works. This guide helps security leaders understand why fundamental flaws remain the root cause of breaches—and how to turn that reality into a roadmap for measurable improvement.

The Basics are the Breach: Lessons from Real-World Product Security Reviews
In this live virtual session, you’ll explore two years of product testing across healthcare, IoT, industrial, and financial systems—and see how “basic” vulnerabilities continue to cause the biggest damage. Learn how small oversights like default credentials, broken cryptography, and insecure configurations can be chained into full-scale breaches, and what you can do to stop them.

AI & LLM Security Testing Datasheet
Understanding your exposure is essential to building secure and resilient AI systems. Bishop Fox AI/LLM security assessments provide the experience and expertise to help you navigate this emerging threat landscape.

Demystifying 5G Security: Understanding the Registration Protocol
In this hands-on workshop, Senior Security Consultant Drew Jones will break down the fundamentals of the 5G registration protocol, explore where security gaps can emerge, and walk through a live simulated lab demonstrating real-world vulnerabilities.

Fireside Chat - SaaS Security: Inside Recent Attacks Disrupting Global Enterprises
Two recent cyberattacks crippled global enterprises by exploiting Salesforce OAuth mechanisms. Join CISO Christie Terrill and former Salesforce security leader Brian Soby for an exclusive breakdown of these breaches and actionable defense strategies in this live fireside chat.

CloudFox: Cloud Enumeration for Penetration Testing
In this session, Mitchell Sperling, Senior Security Consultant at Bishop Fox, will demonstrate how he uses CloudFox during cloud penetration tests to quickly enumerate large cloud environments and identify interesting attack paths.
This site uses cookies to provide you with a great user experience. By continuing to use our website, you consent to the use of cookies. To find out more about the cookies we use, please see our Privacy Policy.